
In this data-centric world of the present day, one cyber leak can compromise millions of users and organizations. One such recent and disturbing trend is the thejavasea.me leaks AIO-TLP287 — an incident that created waves within the cybersecurity circles.
This in-depth article has been put together with the intent to let you know what exactly transpired, what got leaked, what the risks are associated with it, and how people and businesses can safeguard themselves against such occurrences in the future.
Defining Thejavasea.me
Thejavasea.me is a mysterious and now notorious website that purportedly emerged on underground forums and the dark web. The website acts as a data dump repository and distribution hub for leaked data dumps, providing extensive data collections for nefarious purposes.
From login credentials to business secrets, the site has been linked to various massive-scale leaks, including the widely debated AIO-TLP287 dataset. While it looks like a low-profile platform, thejavasea.me is actually quite sinister.
It has emerged as a popular source among cybercrooks searching for confidential data, frequently packaged in obfuscatory terminology such as “AIO-TLP287,” which is short for “All-In-One Threat Level Protocol 287” — a moniker used throughout the cybersecurity community to label intelligence about notable leaks.
Decoding AIO-TLP287
AIO-TLP287 is a leaked collection of enormous datasets which, allegedly, came from several breaches. “AIO” (All-In-One) implies that the information is not from a single entity but is a compilation of different breached sources.
TLP is the Traffic Light Protocol, a cybersecurity community system for ranking threat intelligence. The 287 may be a batch or file number, although the true origin is unknown.
The TLP label here can also be used deceptively to make the dataset seem like something that’s shared in secret security circles—when, in actual fact, it’s being shared with anyone who’s willing to get to it.
What Is Contained In The Javasea.me Leaks AIO-TLP287?
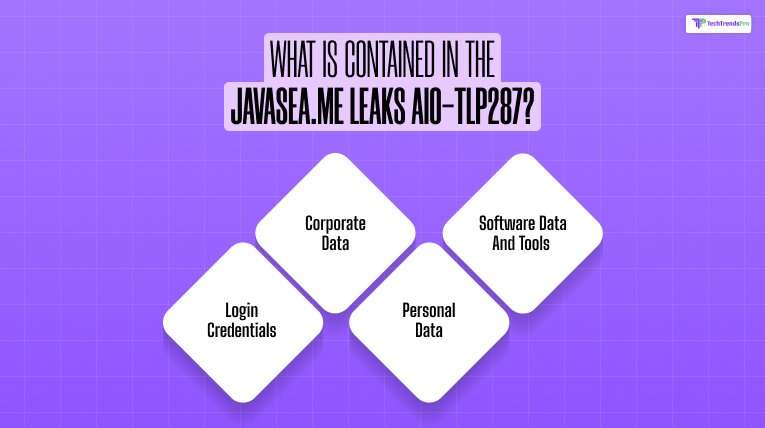
AIO-TLP287 is now infamous for its depth and scope of breached data. From what cybersecurity analysts and ethical hackers have reported, here’s a closer inspection of what the data dump contains:
1. Login Credentials
The dump consists of millions of email-password pairs, a large number of which are plaintext.
The credentials are thought to originate from prior breaches on:
- Social media websites
- Online banking sites
- Streaming services
- Corporate intranets
This information can be used with ease in credential stuffing attacks, where attackers utilize stolen login details to gain access to accounts on other sites.
2. Corporate Data
Company networks were not left behind either.
Files included in the dump are:
- Internal emails
- Business strategy reports
- Cloud storage URLs
- Financial spreadsheets
- API keys and system settings
This type of data, for the wrong individuals, can apply to corporate espionage or sabotage.
3. Personal Data
Maybe the most worrying part is the personally identifiable information (PII), such as:
- Names
- Addresses
- Phone numbers
- Government IDs (e.g., Social Security Numbers, Driver’s Licenses)
- Medical records
This type of information is gold to identity thieves and scammers.
4. Software, Data, And Tools
The AIO-TLP287 leak also contains software packages, cracking tools, and malware scripts — sending up red flags that the leak not just has stolen information, but also tools to cause more damage.
Implications Of The Javasea.me Leaks
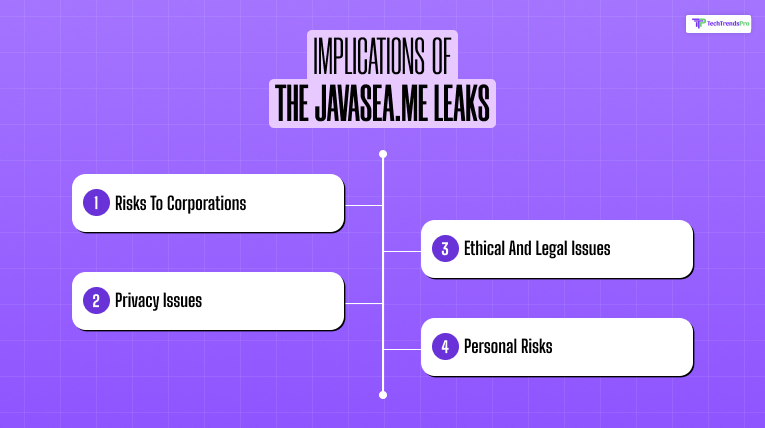
The implications of this leak are far-reaching and impact both users and organizations.
Here’s what the risks look like:
A. Risks To Corporations
- Intellectual Property Loss: Disclosed strategic papers and R&D information can result in lost competitive edge.
- Reputation Damage: Customers will lose confidence in a firm that cannot safeguard their information.
- Financial Loss: Both directly in fraud and indirectly through litigation, fines, or ransomware claims.
B. Privacy Issues
- The leak reveals private messages and PII, which breaches users’ rights and subjects them to identity theft and scams.
C. Ethical And Legal Issues
- The presence and dissemination of such datasets give rise to serious concerns regarding digital ethics, consent, and accountability.
- Firms that do not secure user information might encounter regulatory action in terms of laws like GDPR, HIPAA, or CCPA.
D. Personal Risks
- Identity Theft: Compromised government IDs or credit card numbers may be used to create fake accounts.
- Credential Reuse: If people reuse passwords, a single breach could gain access to numerous platforms.
- Targeted Attacks: Cyber attackers might exploit leaked data to attempt phishing, extortion, or social engineering attacks.
How Did The Leak Occur?

Cyber breaches usually are the result of both technical weaknesses and human mistakes. Thejavasea.me breaches AIO-TLP287 are no different.
Here’s how these records may have been breached:
1. Social Engineering
Attackers trick people into sharing sensitive information by posing as authoritative entities.
This might include:
- Pretending to be IT support
- Pretexting a lawful demand
- Leaked information for building credibility
2. Vulnerability Exploitation
Hackers use weaknesses in software, systems, or ancient plugins to gain unauthorized access.
Typical weaknesses are:
- SQL injection
- Zero-day exploits
- Unpatched servers
3. Phishing Attacks
Spam messages or emails that trick victims into clicking on bad links or installing malware. These tend to be the entry point for large breaches.
4. Threats from Insiders
Disgruntled staff must have access to sensitive information, or contractors may deliberately leak information — out of revenge, ideology, or for money.
How To Prevent Future Leaks
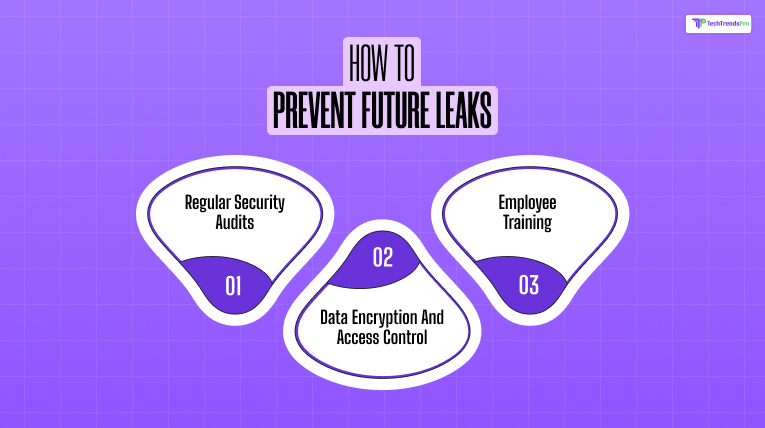
Prevention of data breaches, such as AIO-TLP287 calls for a multi-layered cybersecurity strategy.
This is what can be done by individuals and organizations:
A. Regular Security Audits
- Do vulnerability assessments and penetration tests.
- Update outdated software in a timely manner.
- Track logs for unauthorized attempts.
B. Data Encryption And Access Control
- Encrypt data at rest and in transit.
- Implement role-based access control (RBAC) to restrict exposure.
- Implement multi-factor authentication (MFA) on sensitive systems.
C. Employee Training
- Educate personnel on how to spot phishing and social engineering.
- Set up procedures for reporting incidents.
- Conduct simulated attack attempts to gauge readiness.
Bonus Tip: Use password managers and rotate credentials regularly.
FAQs
Here are a few questions asked by others on the topic thejavasea.me leaks aio-tlp287, that you might find helpful for your knowledge.
It is a huge dataset leaked online through an illicit site (thejavasea.me), including login information, personal details, corporate documents, and tools for hacking — estimated to have been gathered from more than one breach.
No. Thejavasea.me is neither a genuine nor a secure site. It’s associated with unlawful data dumps and possibly dangerous files and must be avoided.
• People whose credentials or disclosing information.
• Organizations whose in-house data or leak staff credentials.
• Anyone recycling passwords between services.
Is thejavasea.me leaks aio-tlp287 Helpful!
The thejavasea.me AIO-TLP287 leaks serves to point to the increasing sophistication and temerity of contemporary cyber threats.
In an age more and more reliant on digital infrastructure, data breaches such as this one reinforce the need for vigilance, proactive security, and ongoing education.
Whether you’re a concerned citizen or a cybersecurity expert, vigilance is your best defense. If you think your information is potentially in the AIO-TLP287 breach, change your passwords.
Turn on two-factor authentication, and look into identity monitoring services. Information may be the new oil — but like oil, when it spills, the devastation can be apocalyptic.
Additional Resources:






