
Would you believe there are vulnerabilities in your wireless networks no matter how secure you think it is? Or that set up what’s known as an ‘Evil Twin’ network (which not only looks like but actually has all the properties of your network) is all it takes to gain access to critical data within your network?
Believe it or not, your network isn’t as secure as you think from this type of cyber threat. Fortunately, the good news is IT support firms like EC-MSP can help you regularly conduct security audits to ensure your business and its’ wireless network remain safe from cyber-attacks.
Let’s explore how your business’ wireless security can be compromised by the Evil Twin attack, and what your IT support provider can do to prevent it.
Are your wireless networks truly protected from cyber-attacks?
Cyber security is how individuals and organizations reduce the risk of cyber-attack.
Unlike wired networks that use cables to connect devices such as computers, printers, and servers within a network, wireless networks allow these same devices to remain connected to the network via various wireless methods such as Wi-Fi, Bluetooth, WiMax, LTE, and so on.
Figure 1: A wired network
Figure 2: A wireless network
Wireless networks present an overwhelming number of benefits when compared to wired networks, including mobility of devices, convenience to access network resources within the wireless coverage area, and easy setup. Despite these advantages over wired networks, they are easily compromised by an Evil Twin attack.
Is your network secure enough to withstand The Evil Twin attack?
The Evil Twin is a wireless network that carries the same name and properties of the wireless network to be attacked. It’s the most dangerous wireless threat that has lasted over two decades. Once this rogue network is set up, a victim’s devices are tricked into associating with it. As an experiment, I set up an Evil Twin network, created four secured wireless networks, and then tested them against this attack. The verdict? They were all susceptible.
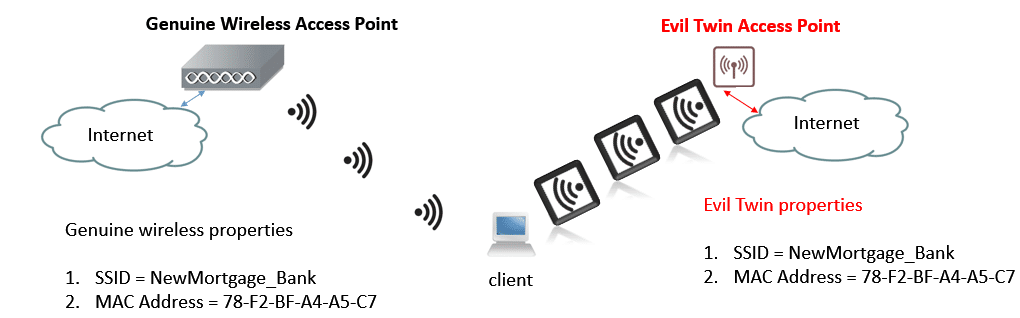
Figure 3. The Evil Twin access point
What are the components of an Evil Twin?
- A rogue access point with at least the same Service Set Identifier (SSID) and MAC address is set up.
- The rogue access point is maintained close to the clients being attacked.
- The signal level of the rogue access point is maintained at the highest levels possible.
- The rogue access point sends de-authentication packets, thereby forcing all clients connected to the genuine network to disassociate from it.
- The clients disconnected from the genuine network sends authentication hashes to the rogue access point.
- Once disconnected, a client may retype the wireless password thinking it is reconnecting with the genuine network.
- The wireless password gets compromised and the client’s activities are monitored and manipulated so long as data goes through the rogue access point.
The solution to Evil Twin attacks: Wireless Intrusion Prevention System (wIPS)
Evil Twin access points are nearly impossible to detect because their SSID and MAC addresses match those of a genuine network. To keep these attacks to a minimum, Wireless Intrusion Prevention Systems (wIPS) must be deployed in corporate wireless networks.
wIPS is a wireless network security solution that operates at layer 2 of the Open System Interconnect (OSI) model. This solution scans wireless networks and monitors the radio spectrum for rogue access points, misconfigured devices, and other wireless threats.
wIPS takes note of all wireless networks and access points within its reach and raises an alert when anything unusual is detected. The architecture for wIPS can be categorized as either centralized or decentralized. In centralized wIPS, wireless local area network (WLAN) traffic is collected by sensors and then sent to a centralized management system where the WLAN traffic is processed. This central point also handles the logging of threats and alerting of system administrators to respond to logged treats. In decentralized wIPS, there are different systems that handle both logging and alerting functions.
Irrespective of how they’re categorized, wIPS can be deployed in three basic ways:
Slicing of time
In this type of deployment, the same access point that connects to the genuine network slips from its duty of serving wireless clients to scanning for rogue access points and then returns to its original duty. This architecture causes a genuine access point to be overloaded with work.
Integrated scanner
In this type of deployment, a sensor that continually scans the radio spectrum for rogue access points is integrated in the genuine access point. This architecture reduces the overload of the genuine access point.
Overlay
In this deployment, dedicated wIPS sensors are deployed. These sensors have the primary purpose of only scanning for rogue access points and they are independent of the genuine access point serving the wireless clients. Though the best deployment, it is more expensive as it requires dedicated hardware.
wIPS detects rogue access points by continuously capturing and filtering raw wireless frames. The intrusion system discards all frames directed to other access points. After filtering, the system also classifies the access points detected in the radio spectrum as:
Authorized – if they’re known and connected to the genuine network.
External or Neighboring – if they’ve been detected within the genuine network’s air space.
Rogue – if they’re connected to the genuine network but unknown.
These classifications serve as the foundation for enforcing wireless security policies.
In order to prevent Evil Twin Attacks, wIPS keeps a record of all connected clients within the genuine network by monitoring each client’s MAC address and storing them in a database.
If a client within the genuine network attempts to establish a connection with a rogue access point, the connection is instantly blocked using a de-authentication packet.
Drawbacks of wIPS
Even though the benefits to a wireless Intrusion Prevention System can be numerous, there’s one major drawback that needs to be considered before deploying wIPS.
Some wIPS are not able to properly classify access points detected within the radio spectrum during scans. If access points are not properly classified and mistakenly shut down because they were tagged as a rogue, corporate organizations run the risk of legal sanctions.
Given the risk of being sanctioned for mistakenly shutting down another organization’s access point, it may be recommended to rely on the manual classification of access points which can be time-consuming. Your time and money are well-spent employing an external, expert IT support team to take care of this for you.
Read Also:






